Cryptography is a crucial component of cryptocurrency, providing a secure and private method of conducting transactions. With the rise of cryptocurrencies like Bitcoin and Ethereum, there has been an increased focus on the importance of cryptography in safeguarding digital assets. In order to properly understand and utilize cryptocurrencies, it is essential to have a comprehensive understanding of cryptography.
NeoReach, a leading platform for influencer marketing, has recently released The Ultimate Cryptography Guide for Cryptocurrencies. This comprehensive guide aims to provide a complete overview of cryptography and its application in the world of cryptocurrencies.
The Ultimate Cryptography Guide for Cryptocurrencies covers a wide range of topics, including the history of cryptography, the basics of encryption, and the role of cryptography in securing digital currencies. The guide also delves into the various types of cryptographic algorithms and their use in cryptocurrency transactions. Additionally, the guide explores the concept of public and private keys, as well as the process of digital signatures in cryptocurrency transactions.
One of the key highlights of the guide is its in-depth coverage of blockchain technology and its relationship with cryptography. The guide explains how the blockchain, which serves as the public ledger for all cryptocurrency transactions, relies heavily on cryptographic principles to ensure the security and integrity of the network.
Furthermore, The Ultimate Cryptography Guide for Cryptocurrencies provides insights into the current challenges and future developments in cryptocurrency cryptography. As the cryptocurrency landscape continues to evolve, it is important for users to stay informed about the latest advancements in cryptographic techniques and security measures.
NeoReach’s guide is a valuable resource for both beginners and experienced cryptocurrency enthusiasts. It serves as a comprehensive reference for anyone looking to gain a deeper understanding of the underlying cryptographic principles that power the world of digital currencies.
In addition to providing educational content, NeoReach also offers practical insights into the practical applications of cryptography in the context of cryptocurrency marketing. As a leading influencer marketing platform, NeoReach understands the importance of maintaining secure and transparent transactions in the cryptocurrency space.
Overall, The Ultimate Cryptography Guide for Cryptocurrencies is an essential resource for anyone looking to enhance their knowledge of cryptography and its role in the cryptocurrency industry. With its comprehensive coverage of key concepts and practical applications, this guide is a valuable tool for individuals and businesses alike. Whether you are a cryptocurrency investor, a blockchain enthusiast, or a marketing professional looking to leverage the power of cryptocurrencies, NeoReach’s guide is a must-read for all.
Cryptocurrency has stuck around through thick and thin, but one term stands as a bulwark against malicious actors and potential financial disaster: cryptography. This article seeks to illuminate the critical role of cryptography in the realm of digital assets in an easy-to-follow cryptography guide.
Did you know that NeoReach runs world-class influencer marketing campaigns? Check out our case studies here!
What is Cryptography?
Cryptography, in the context of cryptocurrencies, refers to the science and art of securing digital information through the use of complex mathematical algorithms. This system ensures that sensitive data remains confidential, is transmitted securely, and is resistant to unauthorized access or tampering. The intricate network of cryptographic principles forms the backbone of modern blockchain technology and the security infrastructure for digital assets.
Foundations of Cryptography
The foundation of any cryptography guide begins with a comprehensive understanding of encryption, the cornerstone of digital security. Encryption converts plain text into an unintelligible format using a key, making it nearly impossible for unauthorized parties to decipher. This article delves into this fundamental concept, introducing the building blocks of cryptographic techniques, such as asymmetric encryption and symmetric encryption.
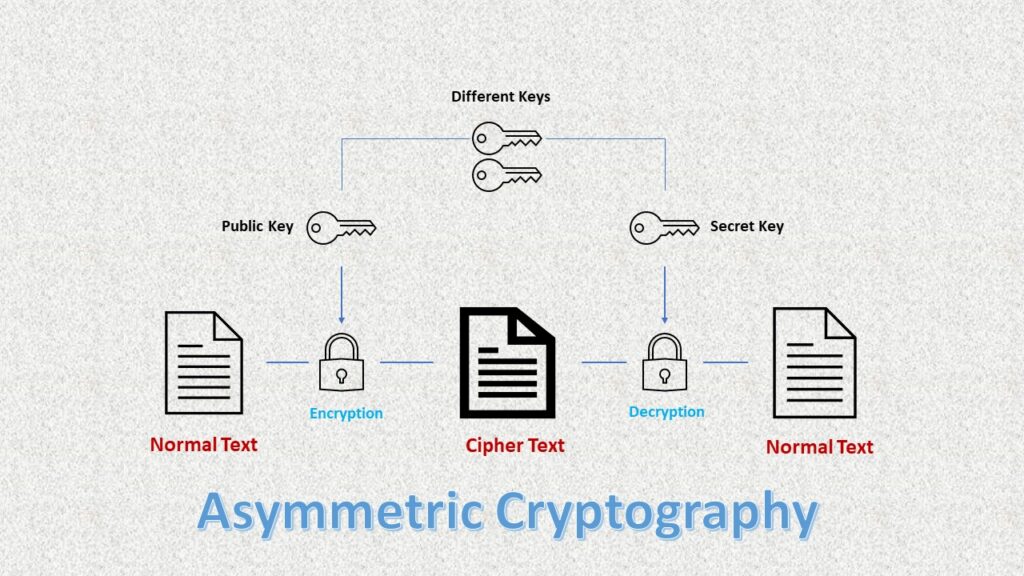
Asymmetric encryption employs two distinct keys, one for encryption and one for decryption. These keys, a public key and a private key, play an integral role in securing cryptocurrency transactions. The cryptography guide emphasizes that the public key is shared openly, while the private key is kept secret. When someone sends cryptocurrency to another user, they employ the recipient’s public key to lock the funds securely. Only the recipient, with access to their private key, can unlock and access the funds.


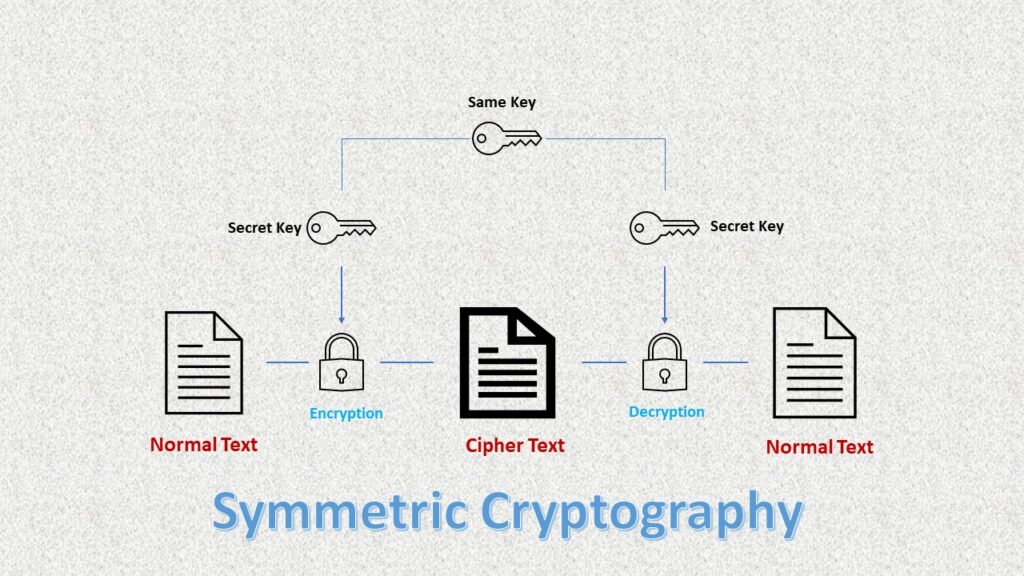
Symmetric encryption, on the other hand, employs a single shared key for both encryption and decryption. While it is typically faster than asymmetric encryption, it comes with the challenge of securely exchanging the key between the sender and the recipient. The cryptography guide highlights the importance of secure key exchange methods in maintaining the confidentiality of digital assets.


Digital Signatures and Hash Functions
Our cryptography guide continues by exploring two other vital components in the world of cryptocurrencies: digital signatures and hash functions. These cryptographic elements play a critical role in ensuring the integrity of blockchain transactions and protecting crypto users’ assets.
Digital signatures are cryptographic algorithms that provide proof of the authenticity of a transaction or message. The cryptography guide underscores that every cryptocurrency transaction includes a digital signature created using the sender’s private key. The recipient can use the sender’s public key to verify the signature’s authenticity, ensuring that the transaction has not been tampered with and originates from the rightful sender.
Hash functions, as explained in the cryptography guide, are one-way mathematical transformations that convert data into a fixed-length string of characters. The resulting hash value is unique to the input data, making it nearly impossible to reverse-engineer the original information. Hash functions are instrumental in ensuring data integrity in the blockchain by verifying that the stored data remains unaltered.
Do you love investing in crypto? Check out these eco-friendly cryptocurrencies at this NeoReach blog!
The Importance of Cryptography in Real-World Scenarios
To emphasize why crypto users should know cryptography to protect their assets, let’s examine a few real-world case studies:
The Mt. Gox Hack
One of the most infamous events in cryptocurrency history was the Mt. Gox hack in 2014. This exchange lost over 850,000 bitcoins, valued at the time at $450 million. The breach occurred due to a lack of proper security practices, including inadequate encryption and storage of private keys. This case underscores the importance of securing private keys and the role of cryptography in protecting assets. After the hack culprits were revealed in 2014, Mt. Gox shut down.



The Parity Wallet Bug
In 2017, a vulnerability in Parity’s multi-signature wallet led to the loss of approximately 513,000 ether, worth around $150 million at the time (the number has since increased to $280 million). The bug allowed a user to accidentally lock everyone out of the wallet’s funds. Understanding cryptographic best practices could have prevented this catastrophic event, as the vulnerability was a result of improper key management.
The Twitter Bitcoin Scam
In July 2020, numerous high-profile Twitter accounts were compromised, and a cryptocurrency scam swept through the platform. The attackers leveraged social engineering tactics to gain control of accounts and solicit Bitcoin donations. Although not a direct cryptography issue, this case highlights the need for better user education and security awareness, which a strong cryptography guide can bolster.
The Stake Hack
While we previously discussed the Stake hack and the potential consequences upon Kick streaming, a well-known competitor for Twitch and YouTube streaming, it’s important to reassess the damages. In early September 2023, over $41 million was stolen from Stake digital wallets, which affected cryptocurrencies like Ethereum, Polygon, and BNB Chain. The Stake hack stemmed from a massive security breach, which wasn’t publicly addressed until 5 hours after withdrawals occurred.
It’s uncertain where these stolen assets went. However, the FBI identified the group of hackers as well as their previous hacks on crypto wallets. Others have speculated that the group reigns in North Korea, which suggests more sinister security breaches in the future if protection and privacy are jeopardized.
All services have resumed! Deposits & withdrawals are processing instantly for all currencies. We apologise for any inconvenience. 🙏
— Stake.com (@Stake) September 4, 2023
Why Crypto Users Should Know About Cryptography
Understanding the principles laid out in this cryptography guide is essential for every crypto user. Cryptography is the backbone of security in the digital asset space. Without a grasp of these concepts, crypto users risk falling prey to hackers, fraud, and other malicious actors seeking to exploit vulnerabilities in the cryptocurrency ecosystem.
Moreover, knowledge of cryptography empowers crypto users to take charge of their security. With an understanding of how cryptographic keys and digital signatures work, users can better protect their private keys and ensure the authenticity of transactions. In the world of cryptocurrencies, personal responsibility is paramount.
Learn how to protect your digital assets at this NeoReach blog!
Influencer Marketing and Cryptography
In the world of cryptocurrencies, influencer marketing has gained significant traction. Crypto influencers wield considerable influence over their followers and can shape perceptions, opinions, and investment decisions. Given the importance of security in the crypto space, influencers who are well-versed in cryptography have a unique advantage.
Likewise, influencers who possess a deep understanding of the principles outlined in this cryptography guide can better educate their followers on security best practices. They can emphasize the importance of safeguarding private keys, using hardware wallets, and practicing good cybersecurity hygiene. Their guidance can help protect the assets of countless crypto users, making them more resilient to potential threats.
Final Thoughts on Cryptography
We hope this cryptography guide has shed light on the pivotal role of cryptography in securing digital assets in the world of cryptocurrencies. Understanding encryption, digital signatures, hash functions, and other cryptographic principles is paramount for every crypto user. The knowledge gained from this guide empowers users to take control of their security and make informed decisions, safeguarding their wealth effectively.
As influencer marketing continues to shape the space, influencers with a deep understanding of cryptography can be instrumental in disseminating security information. In doing so, they contribute to a safer and more resilient crypto ecosystem, promoting responsible digital asset management. By understanding these examples, crypto users can see the direct consequences of inadequate cryptography knowledge and the vital importance of understanding and implementing cryptographic principles.
